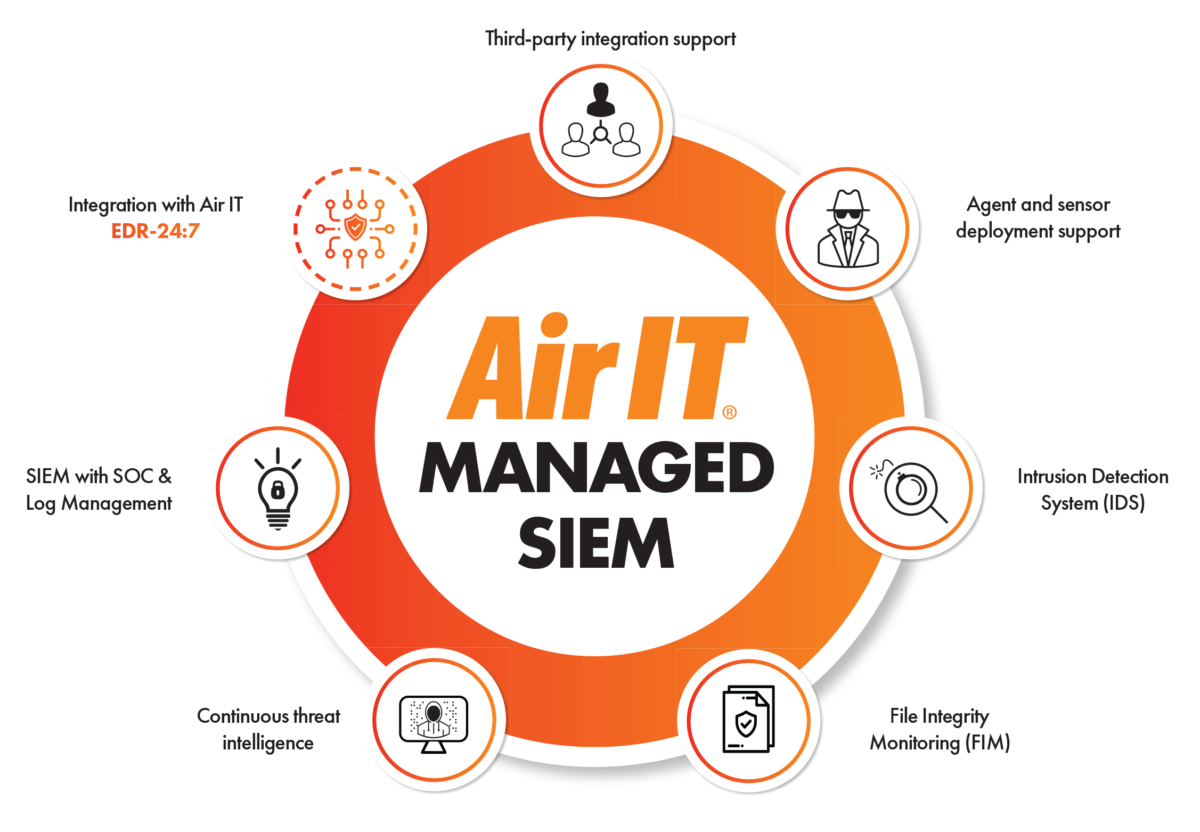
What is SIEM?
SIEM – which is just as weird to pronounce as it looks – stands for Security Information and Event Management. It’s a common ingredient in any modern cybersecurity setup; an intelligent solution with 4 key roles:
- Collecting data from across a company network
- Compiling and standardising this data
- Rigorously scanning this data for anomalies and threats
- Respond to threats smartly
In an era of new and evolving cyber-threats SIEM’s an invaluable business asset. Yet it isn’t a front-to-back protective solution and isn’t without its drawbacks either. For the average business, SIEM is a colossal, frequently complex solution, requiring regular maintenance and monitoring. In an era of ever-evolving threats, that’s a responsibility most of us could probably do without.